In addition to logging in with a user name and a password, it is also possible to log in via Single Sign-On (SSO).
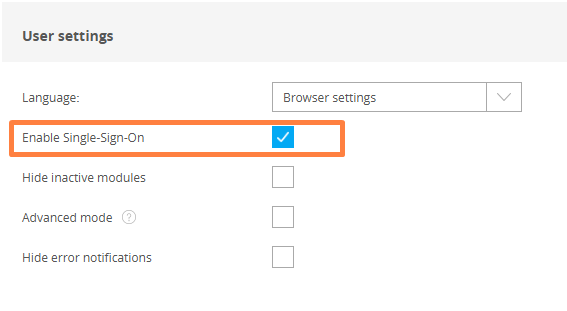
If the property "Enable Single-Sign-On" (in the lower part of the user settings. See screenshot below) of a user is enabled, the user can log in via SSO:
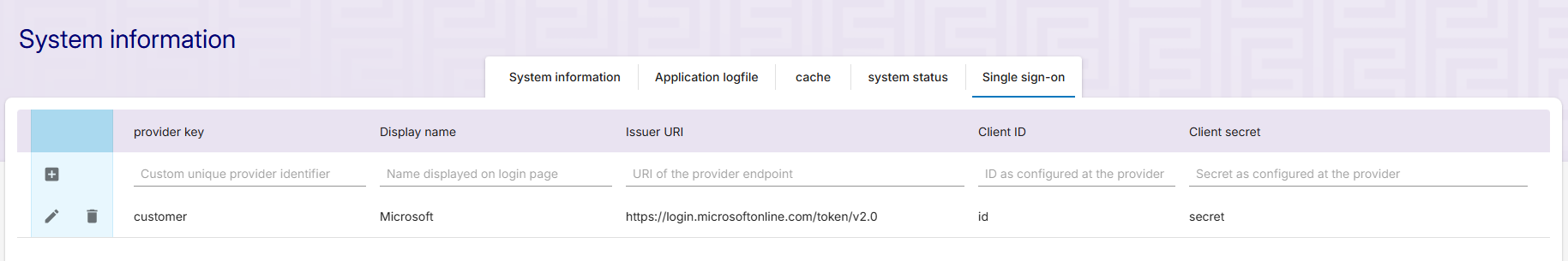
Identity providers (IdPs) for the SSO users can be created and configured at ‘Single-Sign-On settings’ tab of the ‘System information’ page:
Please be aware that clicking the checkmark (see screenshot below) will write your changes to NG's configuration immediately:
The display name of a configured identity provider will be shown on the login page. In our example: to log in via the IdP with the display name "Microsoft" click on "LOG IN VIA MICROSOFT":
.png)
Each configured IdP will display a log-in button on the login page.
If you want to log in with a username and a password, click instead "Log in with credentials". This will bring you to this screen:
.png)
Limitations:
Please be aware that SSO users can neither edit nor create non-SSO users. This is forbidden on purpose. This way it is ensured that users who are no longer employees of the company (and are off-boarded at IdP side) don't keep access to NG and cannot find another way to decouple their accounts from the SSO.
